Web Server Compromise - Apache Struts
Remotely exploiting servers in DMZ's seems so unecessary today with all of the credential theft and client side exploitation, but it is still a critical link in the attack chain. Cloud initiatives are allowing administrators to start up servers all over the place, and most of the time they do not have the same protections in the cloud they typically would in the DMZ. This attack could also be applied for lateral movement if the vulnerable web application is only accessible internally.
Step 1 - Create a subdomain
In Dash create a subdomain called struts, point it to your origin, and ensure the traffic is being proxied (orange clouded).
It will look something like this;

Step 2 - Configure the WAF
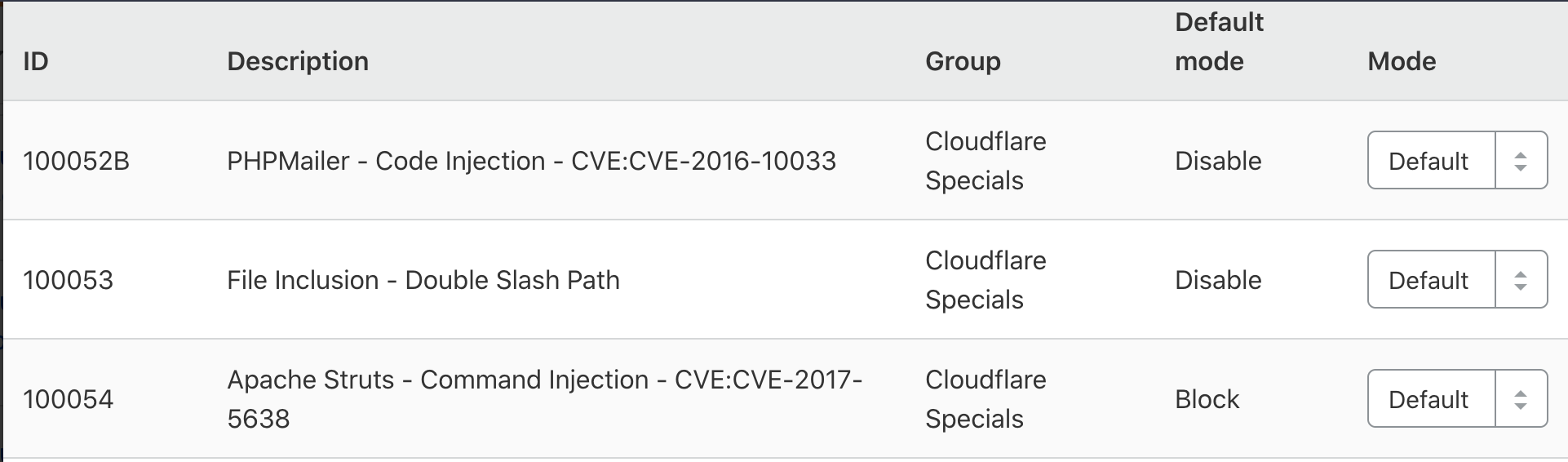
Navigate to Firewall, Managed Rules, Cloudflare Specials.
Find
ID 100054, Apache Struts - Command Injection - CVE:CVE-2017-5638and ensure the action is set to Block.
Step 3 - Deploy the Apache Struts
Typically this container would be added to your GCP infrastructure. The intrstructions to build your own vulnerable container can be found here, https://github.com/freshdemo/ApacheStruts-CVE-2018-11776.
Step 4 - Run the Exploit
From a terminal outside of your origin network, run the exploit against the vulnerable server.
python ./exploit.py http://35.237.118.233:8080 'id'
Your output should look like this, providing nothing was in the way preventing the attack.
root@k:/home/s# python ./exploit.py http://35.237.118.233:8080 'id' [*] CVE: 2017-5638 - Apache Struts2 S2-045 http://35.237.118.233:8080 : [*] cmd: id uid=0(root) gid=0(root) groups=0(root)
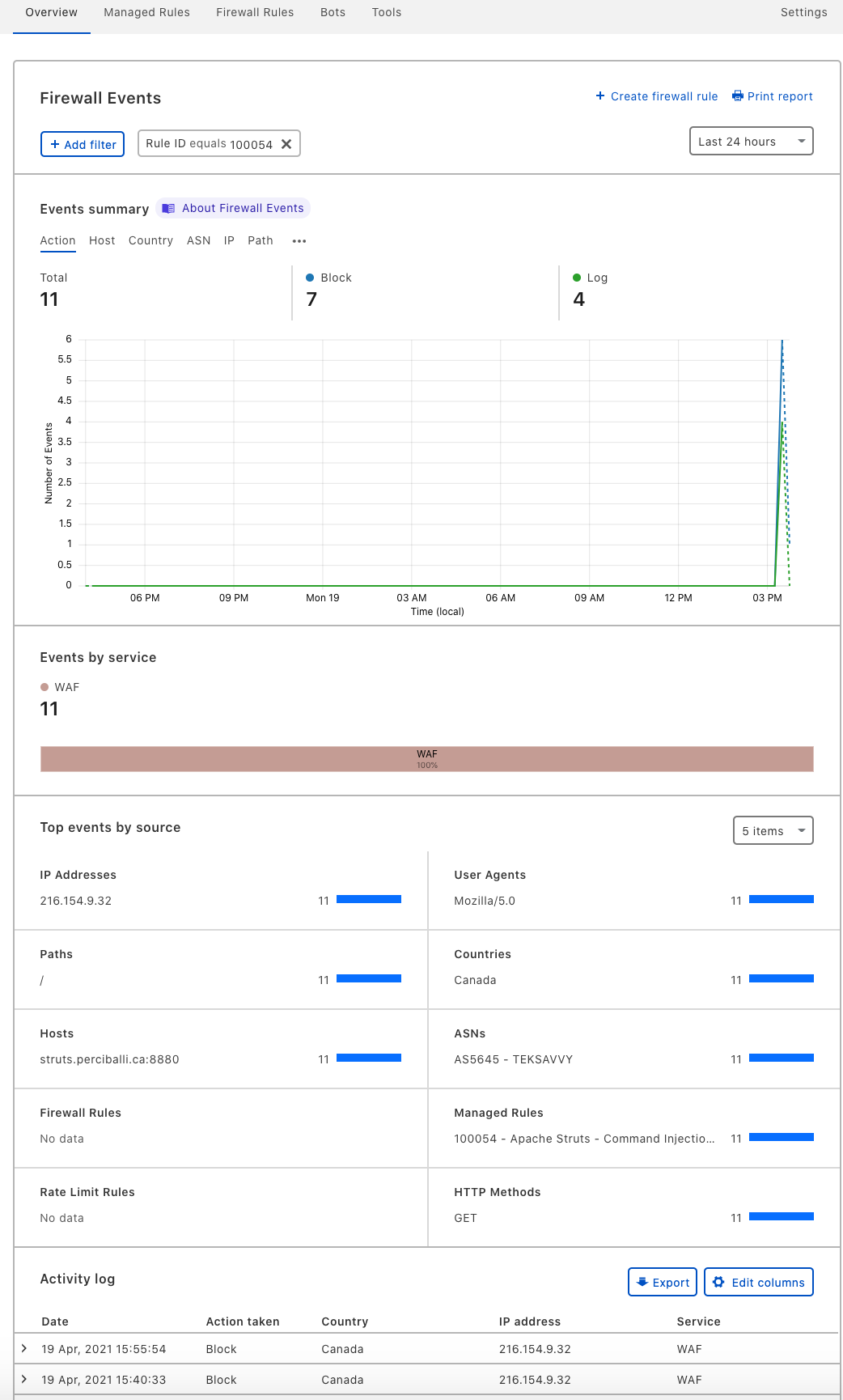
Step 5 - View the Results
Navigate to Firewall, Overview, and scroll down to find Managed Rules. From there you can create a filter for rule ID 100054.