Spearphishing Deploy Malware
Whether the attack is targetted or not, there are times when the adversary wants to deploy malware immediately on the endpoint. Often this will be done by getting them to visit a malicious website or attaching a file.
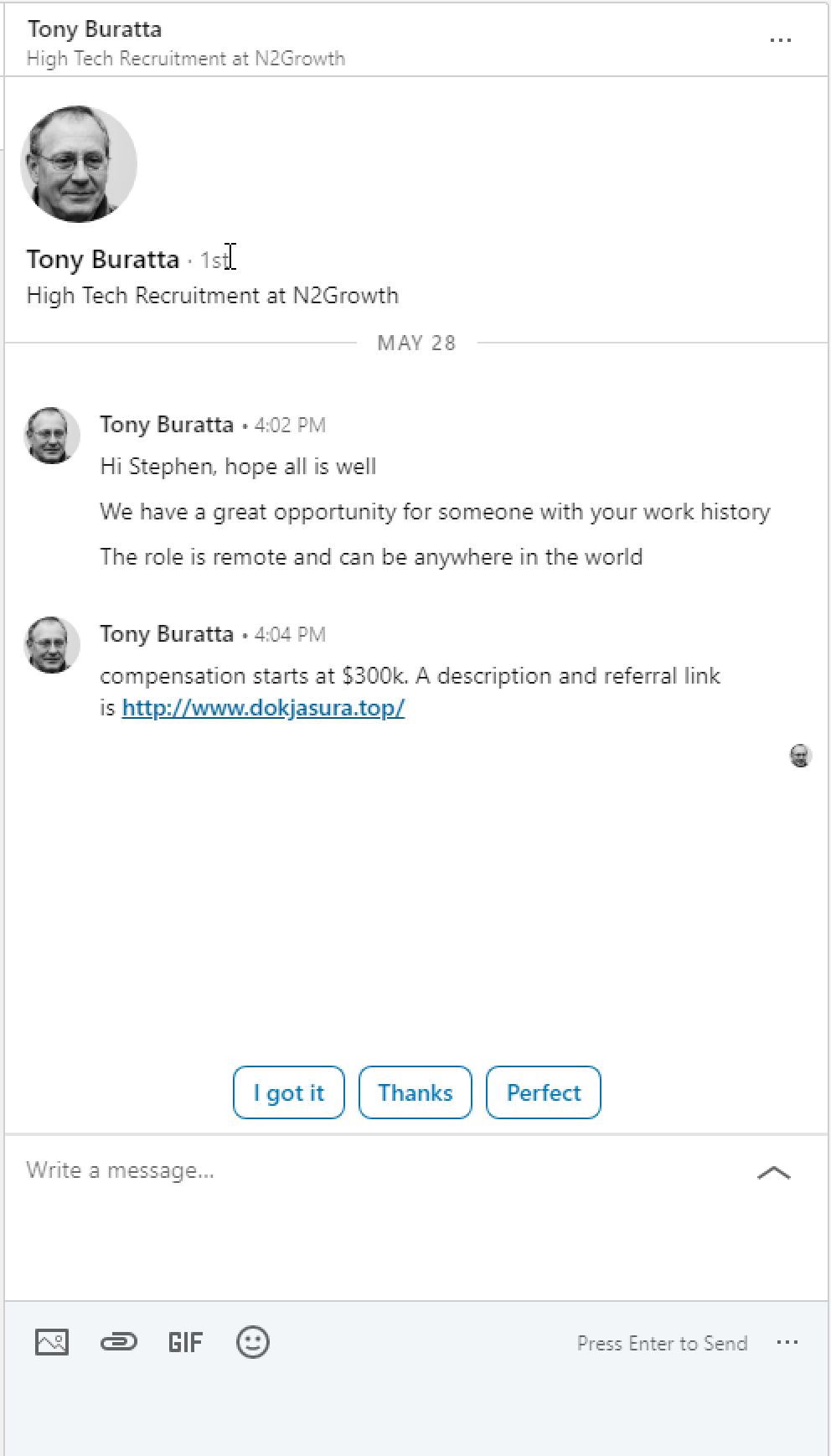
In this use case the adversary has created a LinkedIn profile and sent a very compelling message to their target asking them to click a link.
Step 1 - Setup a Social Media Profile
Use your favorite platform. Sign up for an account. I used a photo from thispersondoesnotexist.com to not bother any real people.
Step 2 - Get a Malware Domain
This part can be tricky, and dangerous. If you want to use a benign dmoain that will generate an alert use https://malware.testcategory.com/.
For a more realistic experience find a known malicious domain in your favourite threat intel feed. An open one is https://www.malwaredomainlist.com/. To ensure that the demonstration is successful, dig the domain first and make sure that Gateway blocks the request before the demonstration. Also be careful with live fire malware. Usually I will access the names from a Linux VM.
Step 3 - Craft the Message
Write a compelling message to your target and send it.
You can see that the malware delivery broke in this case.
Step 4 - View the Protection in Logs
The log below indicates that the domain clicked from the email was sinkholed. This means that when this target computer was asking what the IP address is of the domain even that traffic was dropped. Because it was sinkholed the real IP of the malicious server will not be known to this client so any attempt to connect by name is prevented.
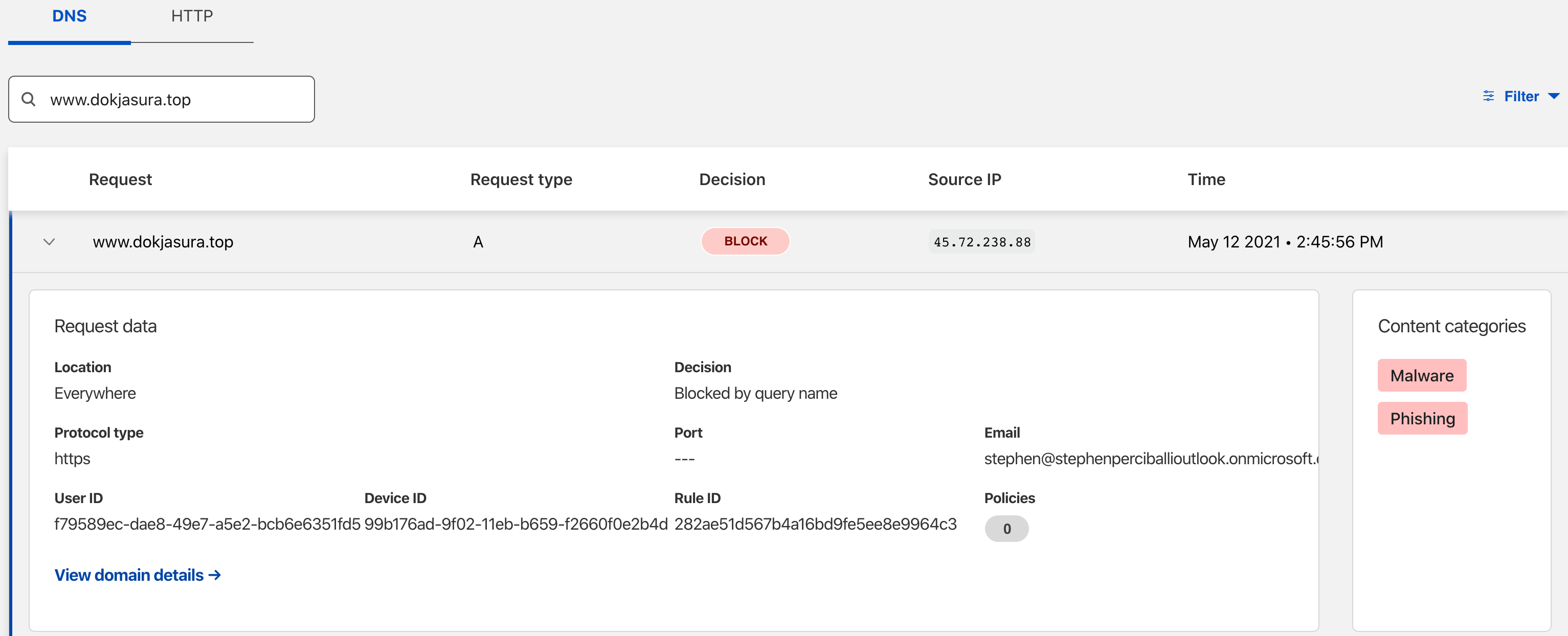 Spearphished Link Sinkhole
Spearphished Link Sinkhole